When performing internal network penetration tests, one thing that really gets us excited is finding administrative consoles. Tomcat and PHPMyAdmin are two of the most common that I’ve found from my experience. The reason we get excited is that many of these consoles have never had the default credentials changed. Why? Because they’re on the internal network! No one would ever attack these systems, right? Well, we would, and do! For example, we were at a large organization doing an internal penetration test and stumbled across a number of servers running Apache Tomcat, indicated by our nmap scans.
8180/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-favicon: Apache Tomcat
|_http-methods: No Allow or Public header in OPTIONS response
|_http-title: Apache Tomcat/5.5
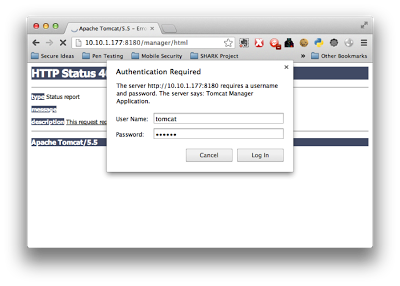
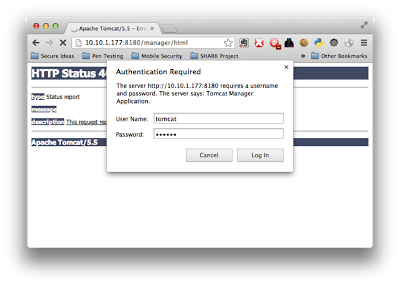
If you don’t already know, the default username and password for the Tomcat Manager is typically tomcat:tomcat. I have found that CIRT.net is a good resource for default credentials for a variety of product web admin consoles, though a simple Google search will also help find other resources as well. For this example, Tomcat Manager is
configured to listen on port 8180. So, we simply use our browser to connect to the server with the correct port number, and are immediately prompted with a Basic Authentication login box.
configured to listen on port 8180. So, we simply use our browser to connect to the server with the correct port number, and are immediately prompted with a Basic Authentication login box.
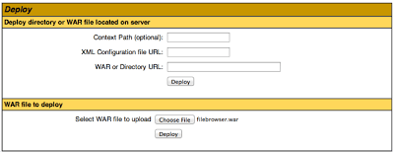
Using the default credentials, we were able to access the Tomcat Manager. Great! But now what? Well, the next thing we wanted to do is see if we could upload our own web application. As you can see from the example below, there are a number of apps already installed, what if we could install our own? This is where we turned to Laudanum. If you’re not yet familiar with it, I recommend reading James Jardine’s blog on the Introduction of Laudanum.
The Tomcat Manager provides the ability to upload a Web Application Archive (WAR) file and then deploy it onto the server. Laudanum has a cmd.war file, which provides the ability to send commands to the operating system, and see the results, from a web browser. James did a follow-up to his Introduction blog called Laudanum by Example: Shell, which demonstrates how to upload the cmd.war file and use it. James also has a video for those who would rather watch than read! Unfortunately, the upload of the cmd.war file was blocked on all the servers during our test. Not giving up, we turned to a really nice jsp File Browser tool by Tobi Vonloesch, which is available as a WAR file on sourceforge, or as a .jsp file on Tobi’s web site.
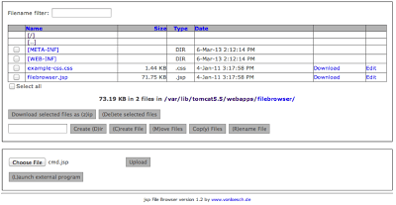
We were able to upload the filebrowser.war file and deploy it as a web app without getting blocked, sweet! Once deployed, the filebrowser jsp app gave us access to the web server’s file system via the web browser by going to http://<serverip>:<tomcat port>/filebrowser/filebrowser.jsp
This web app basically allowed us to navigate the entire file system, as if we were running a file manager directly on the server. It also allowed us to upload cmd.jsp, which is the .jsp file that would’ve been installed if we had been able to upload and deploy the cmd.war file. Most of the servers on this particular engagement were Windows 2003 and
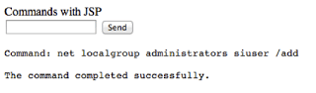
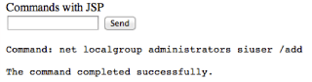
2008 servers, so our next obvious step was to access the command line and see if we could add a user. This was done by creating a new tab on the browser and linking to http://<server ip>:<tomcat port>/filebrowser/cmd.jsp. This resulted in a form where we were able to submit commands to create a user account, siuser, and add our new user account to the local administrators group, using the following commands:
2008 servers, so our next obvious step was to access the command line and see if we could add a user. This was done by creating a new tab on the browser and linking to http://<server ip>:<tomcat port>/filebrowser/cmd.jsp. This resulted in a form where we were able to submit commands to create a user account, siuser, and add our new user account to the local administrators group, using the following commands:
Once we had our account added to the server with local administrator access, we were able to easily login to the server with Remote Desktop Connector. This also led us to uploading and executing a Metasploit payload which provided a Meterpreter session. With Meterpreter, you are able to dump the hashes, and then possibly do a pass
the hash attack against other Windows servers on the network. So, now you know why we get so excited when
we find administrative web consoles on servers, especially those using default creds. It’s just a few steps away from
sweet pwnage!
the hash attack against other Windows servers on the network. So, now you know why we get so excited when
we find administrative web consoles on servers, especially those using default creds. It’s just a few steps away from
sweet pwnage!
Tony DeLaGrange is a Senior Security Consultant with Secure Ideas. If you are in need of a penetration test or other security consulting services you can contact him at tony@secureideas.com or visit the Secure Ideas – Professionally Evil site for services provided.