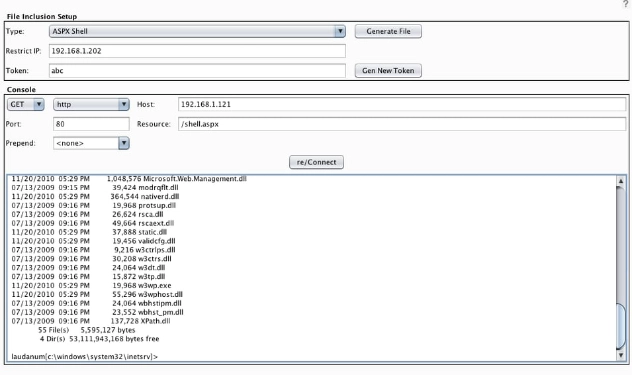
THIS IS IMPORTANT: Remember that just like with classic Laudanum or any other uploaded exploit shell, the console you see is just a pseudo-shell. It is not fully functional in the sense that it can only reliably be used to run a single command at a time. Do not attempt to use it to do complex things like open an interactive command such as vi, or to tail a log file. These types of interactions simply won’t work as expected because the exploit script just executes the given command and responds with whatever is sent to stdout. This being said, it is still quite useful for many situations such as browsing the file system, exploring an internal network, introducing additional exploits, and possibly even setting up a full reverse shell. Laudanum is a great fallback when you can’t directly obtain a shell through MetaSploit.
The latest binary (.jar) for the Burp CO2 suite can be found at http://BurpCO2.com. Updates will periodically be pushed to the BApp Store as they stabilize
Jason Gillam is a Senior Security Consultant with Secure Ideas. If you are in need of a penetration test or other security consulting services you can contact him at jgillam@secureideas.com, on Twitter @JGillam, or visit the Secure Ideas – ProfessionallyEvil site for services provided.