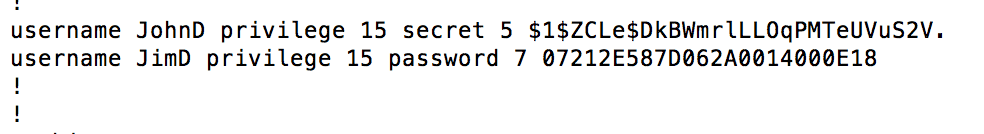
While working on a recent pen test, I came across a few Cisco routers sitting on an internal network. The fact that they were using default cisco/cisco credentials made me cry a little inside, but wait, it gets worse… So I’m in the router, reviewing the running config, and I notice something interesting.
Note that both of these accounts have the same privilege level, but that the passwords are stored differently. This is because the first user was created with a command like this:
Whereas, the second user was created with this command:
The difference between these two storage methods (password or secret) are the hashing algorithms. Type 7 passwords use a very weak algorithm that can be easily reversed, but the “secret” command utilizes a MD5 hash which is much more secure. Due to this, it is never a good idea to use Type 7 passwords. This policy applies to both user accounts and passwords applied to the VTY or Console lines.
So now that I’ve found these Type 7 passwords, I need a way to reverse them. There are several different tools and websites that have this capability, but there’s an easier way! I don’t even have to leave the router! Thanks to a nifty little feature called the “key chain”, I can reverse these passwords right here, right now!
1. First, we will enter config mode:
configure terminal
2. Next, we will create our key chain and give it the name of NEW:
key chain NEW
3. We will enter the first key:
key 1
4. Then we enter the key-string, which will include the number 7 for encryption type and the text of the “encrypted” password:
key-string 7 07212E587D062A0014000E18
* At this point, you may add more keys by repeating steps 3 and 4 if you have multiple passwords to reverse. Make sure to increase the key count though (key 2, key 3, etc.).
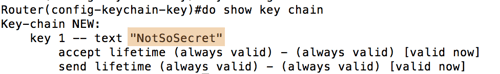
5. Finally, we do a show command, and voila! Passwords!
do show key chain
Now that you’ve seen how incredibly easy it is to reverse these types of passwords, please go forth and check your routers! Ensure that all user accounts and enable passwords listed in the running config are proceeded by the word “secret”.
Donna Fracarossi is a Security Consultant with Secure Ideas. If you are in need of a penetration test or other security consulting services you can contact her at donna@secureideas.com or visit the Secure Ideas – ProfessionallyEvil site for services provided.