Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
SSL Certificates: Setting Up and Authorizing the Internal Certificate Authority
In this post, I wanted to give something directly to the Blue Teams out there. I also thought I ...
Continue Reading
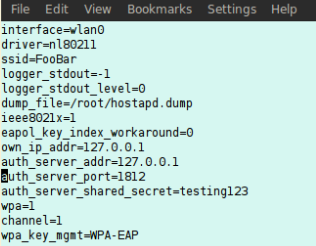
Professionally Evil: This is NOT the Wireless Access Point You are Looking For
I was recently conducting a wireless penetration test and was somewhat disappointed (but happy for ...
Continue Reading
Who We Are: Jason Wood
In this series of posts we are introducing staff members at Secure Ideas to give you a quick ...
Continue Reading
Tactical Security Ops at Black Hat 2013
Kevin Johnson and John Strand recently gave a presentation at RSA 2013 titled “Tactical Sec Ops: A ...
Continue Reading
Looking for Malicious PHP Files
A while back I had to deal with a compromised web server for some folks. They had some WordPress ...
Continue Reading
Reading the Mandiant APT1 Report
Like a lot of folks, I downloaded and read through the Mandiant APT1 report as soon as I could. ...
Continue Reading
Hi, I'm with IT and I'm Here to Steal From You
Beware of the Unknown IT Grunt I decided to continue on with the same theme as Kevin’s post about ...
Continue Reading
Security Onion @ UTOSC 2012
Shortly before joining Secure Ideas, I spoke on Security Onion and Network Security Monitoring ...
Continue Reading