Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
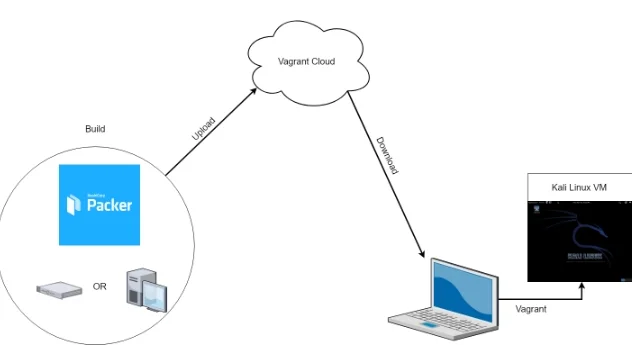
Automating Red Team Homelabs: Part 1 - Kali Automation
Part 2: /2019/05/automating-red-team-homelabs-part-2-build-pentest-destroy-and-repeat.html Homelab ...
Continue Reading
Still SMiShing You - SMS Scams.
Have you ever gotten a strange text message on your phone that you don’t recognize? Well, be ...
Continue Reading
Preventive Security for You
As you go through everyday life, how do you think about your own security? Are you the type of ...
Continue Reading
Security on the Go!
The use of mobile devices is steadily growing. With this increase comes the need for the users to ...
Continue Reading
Introduction to Wireless Security with Aircrack-ng
Today we’re going to walk through a few WiFi testing examples using Aircrack-ng, which is a suite ...
Continue Reading
Escaping the Whale: Things You Probably Shouldn’t Do With Docker (part 2)
This post is part 2 of a series of blog posts on container hacking. If you haven’t read the part1, ...
Continue Reading
Finding Your Weakness: Triaging Your Domains with SWAT
I have been involved in IT and security in one way or another for almost 30 years. I have worked ...
Continue Reading
Defending the Wall: Strong Passwords
Strong passwords are an important part of maintaining accounts and of any organization’s security ...
Continue Reading
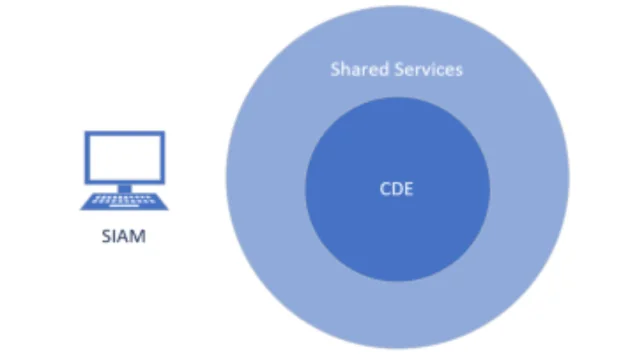
Tips for Penetration Testing a PCI environment
Hello everyone! I put together a list of things to help me keep my PCI testing on track, not to ...
Continue Reading
Three C-Words of Web App Security: Part 1 - CORS
For those less versed in web applications and how they’ve evolved, I wrote a sort of prologue to ...
Continue Reading
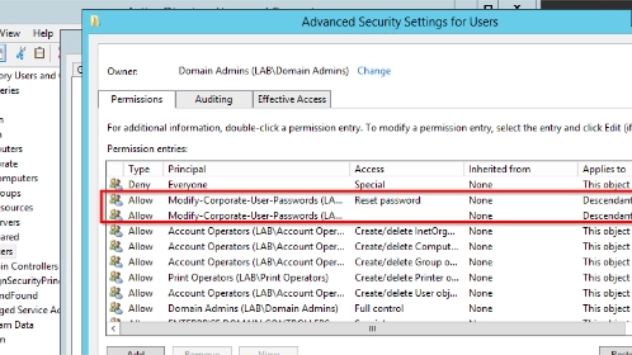
Watching yOUr Permissions
Often, one of the main goals of a pen tester is to get Domain Admin (DA) rights in a client’s ...
Continue Reading