Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
Ransomware Intelligence Briefing
Ransomware Intelligence Briefing Media reporting on the WannaCry ransomware campaign has contained ...
Continue Reading
Protecting your Kids from Online Threats
“The greatest gifts you can give your children are the roots of responsibility and the wings of ...
Continue Reading
Place Your Right Hand On This Glass
One of the hassles of the Yahoo! breach was clearly the coming-home-to-roost quality of the ...
Continue Reading
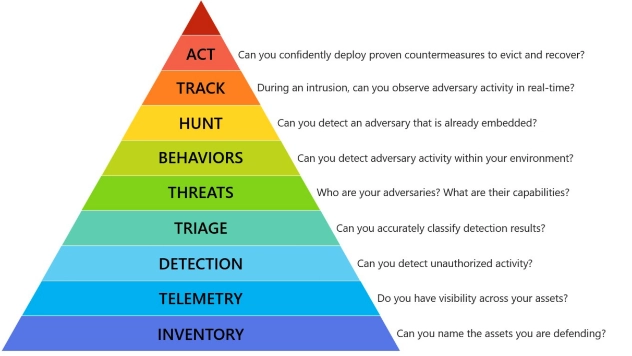
You Must Be This Tall
Imagine going in to do an incident response at a fairly large customer that has no visibility ...
Continue Reading
An Introduction to Javascript for XSS Payloads
I recently got the opportunity to speak at B-Sides Charleston on cross-site scripting (XSS) payload ...
Continue Reading
Statement by Nick Selby on Bishop Fox / Muddy Waters Report
FOR IMMEDIATE RELEASE: Statement by Secure Ideas Response Team Director Nick Selby on the Report ...
Continue Reading
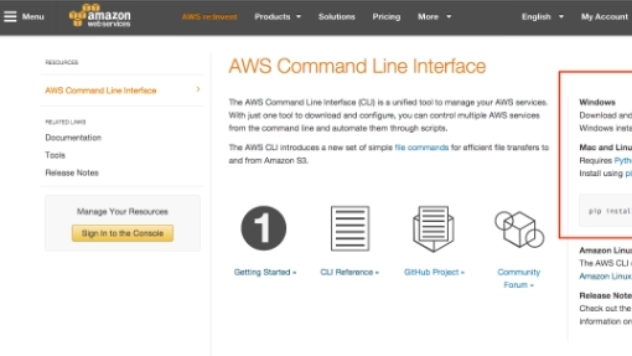
Cloud-Base Host Discovery Is Easier Than You Think!
During a recent conversation at DerbyCon it occurred to me that some security folks who are just ...
Continue Reading
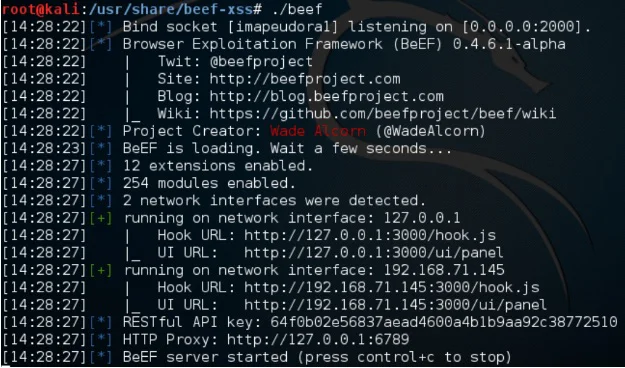
A Brief BeEF Overview
BeEF, the Browser Exploitation Framework, is a testing tool that allows the penetration tester to ...
Continue Reading
Burp Repeater
As a consultant for Secure Ideas there are many tools I use often in my daily tasks. One of the ...
Continue Reading
Hours After The Penetration Test, This CSO Revealed Something That Will Leave You In Tears
We all recognize clickbait when we see it. And yet thousands still click on the links. In today’s ...
Continue Reading
SQLMap Beginnings: What and How
Testing web based applications is not only fun but is often multi-faceted and challenging. Often ...
Continue Reading